
Vulnerability Scanner Showdown: AppDetectivePro 5.4.6 vs. AuditPro Enterprise 4.0 | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More
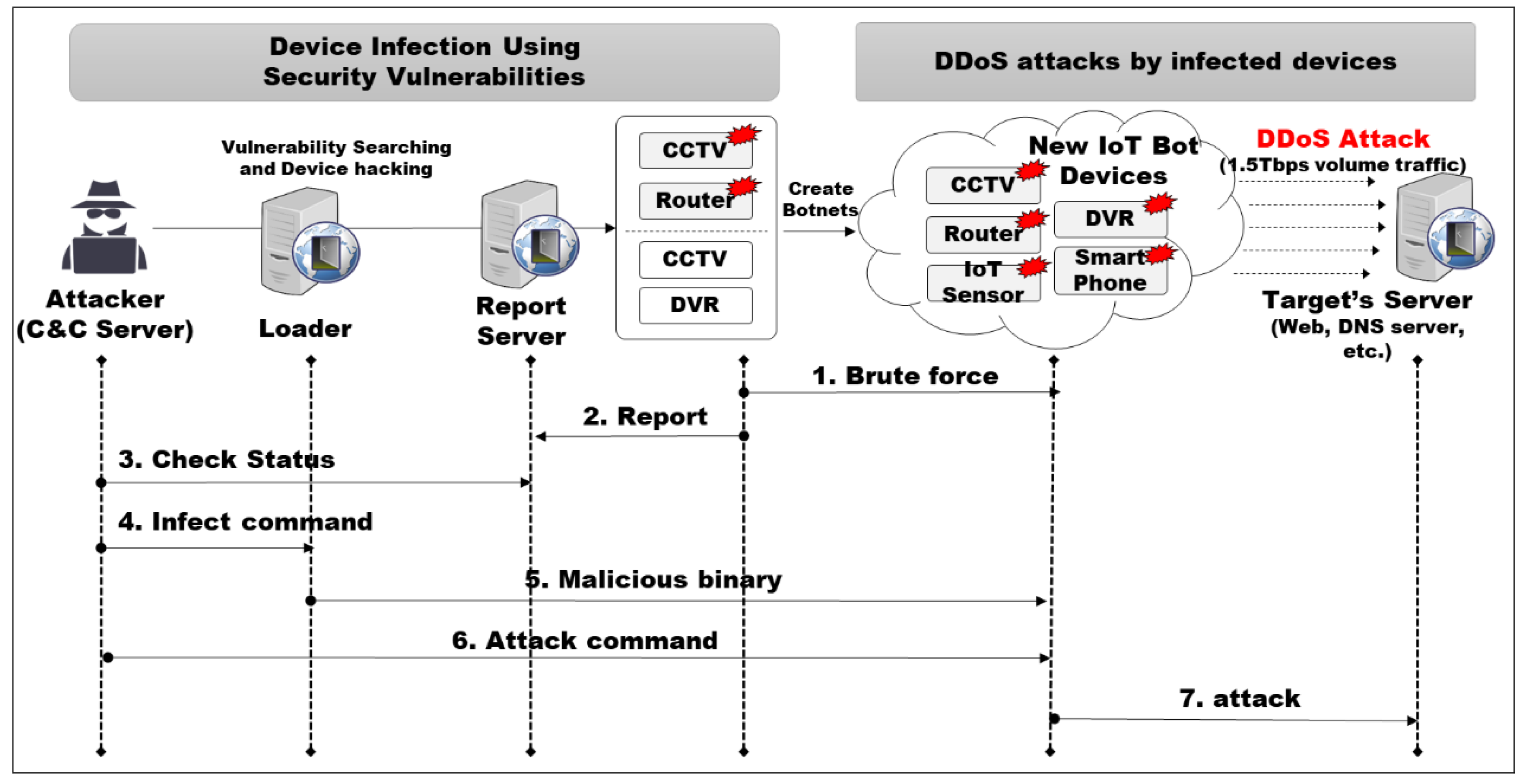
Symmetry | Free Full-Text | An Intelligent Improvement of Internet-Wide Scan Engine for Fast Discovery of Vulnerable IoT Devices

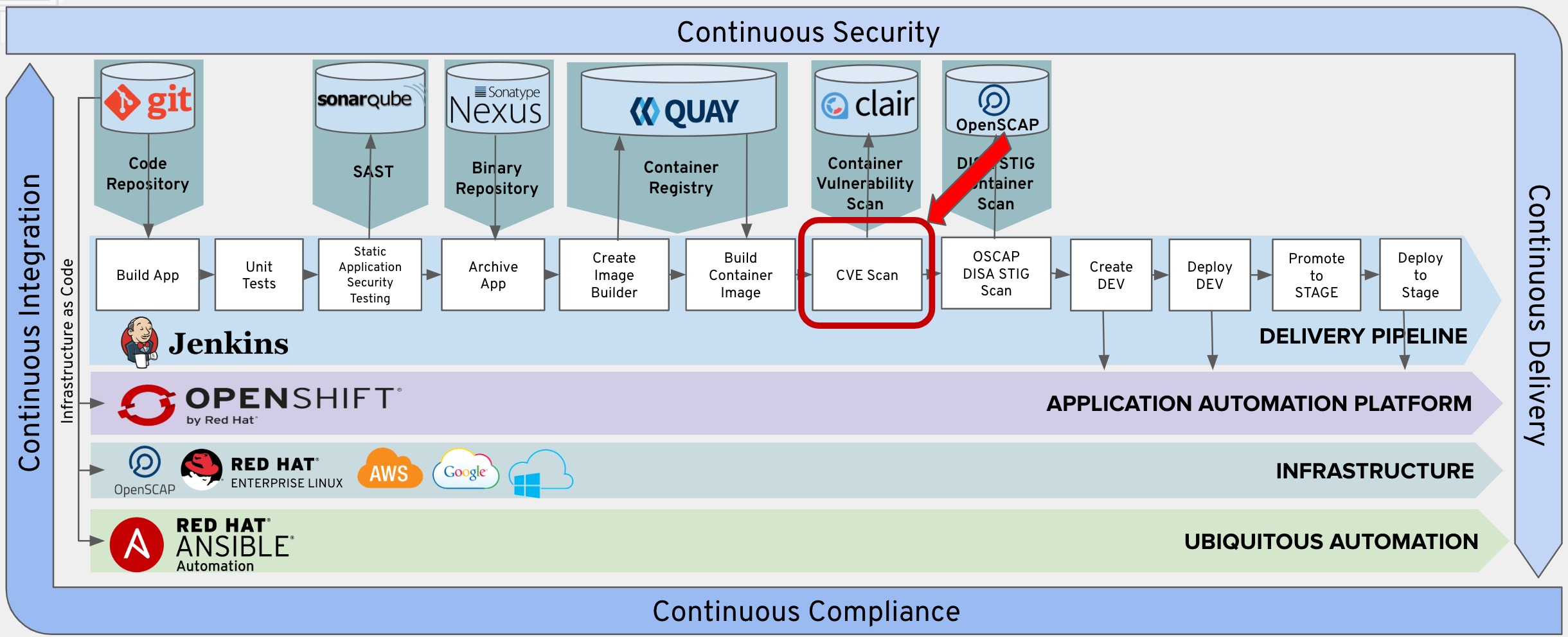
Binary Authorization | Google Cloud | by Prasanna Bhaskaran Surendran | Google Cloud - Community | Medium




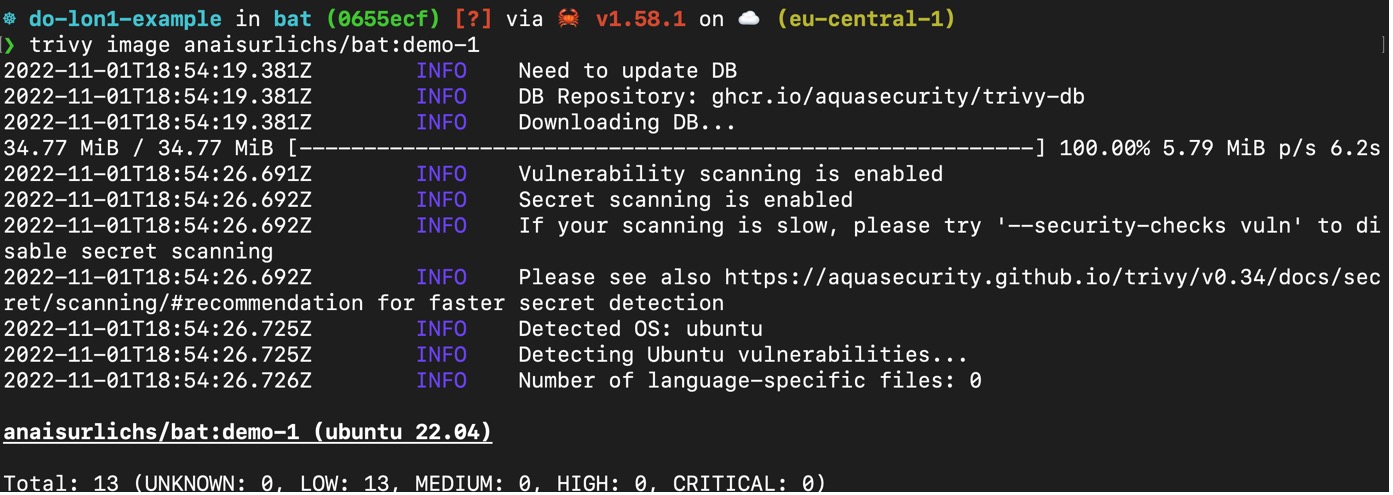

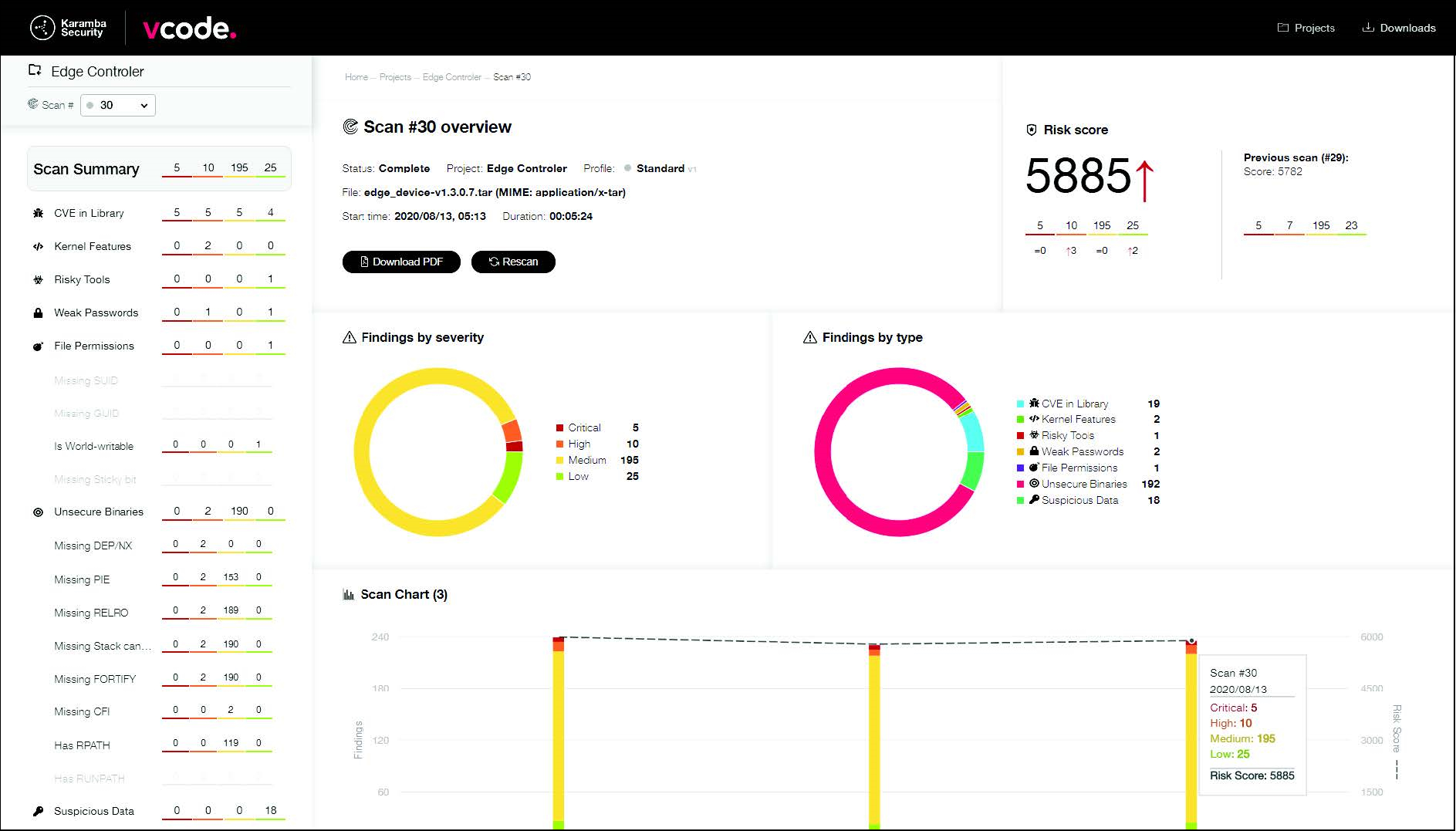

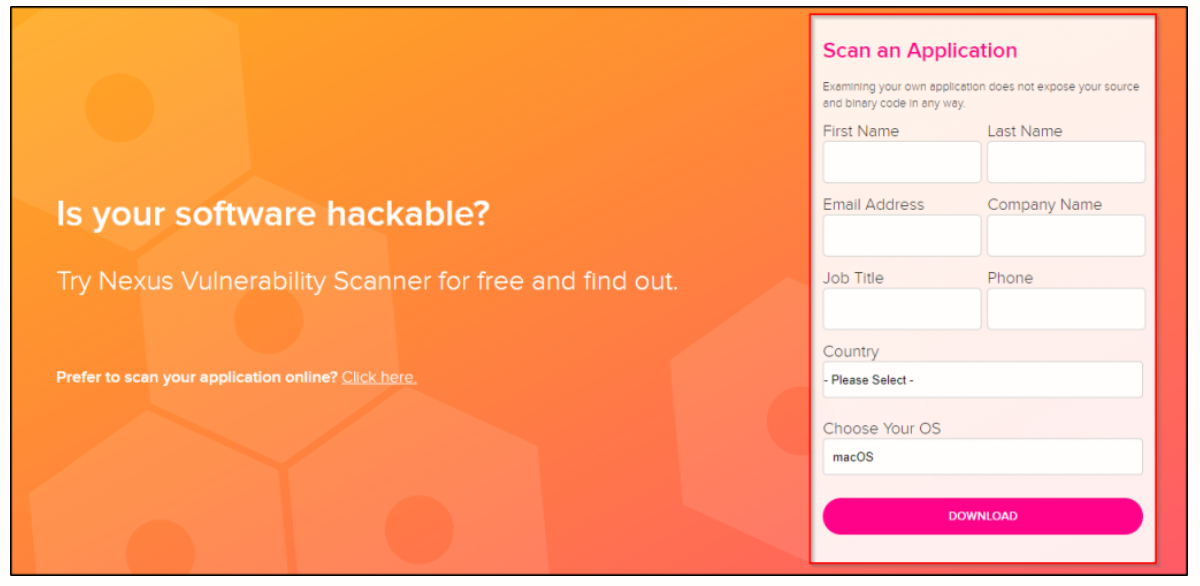


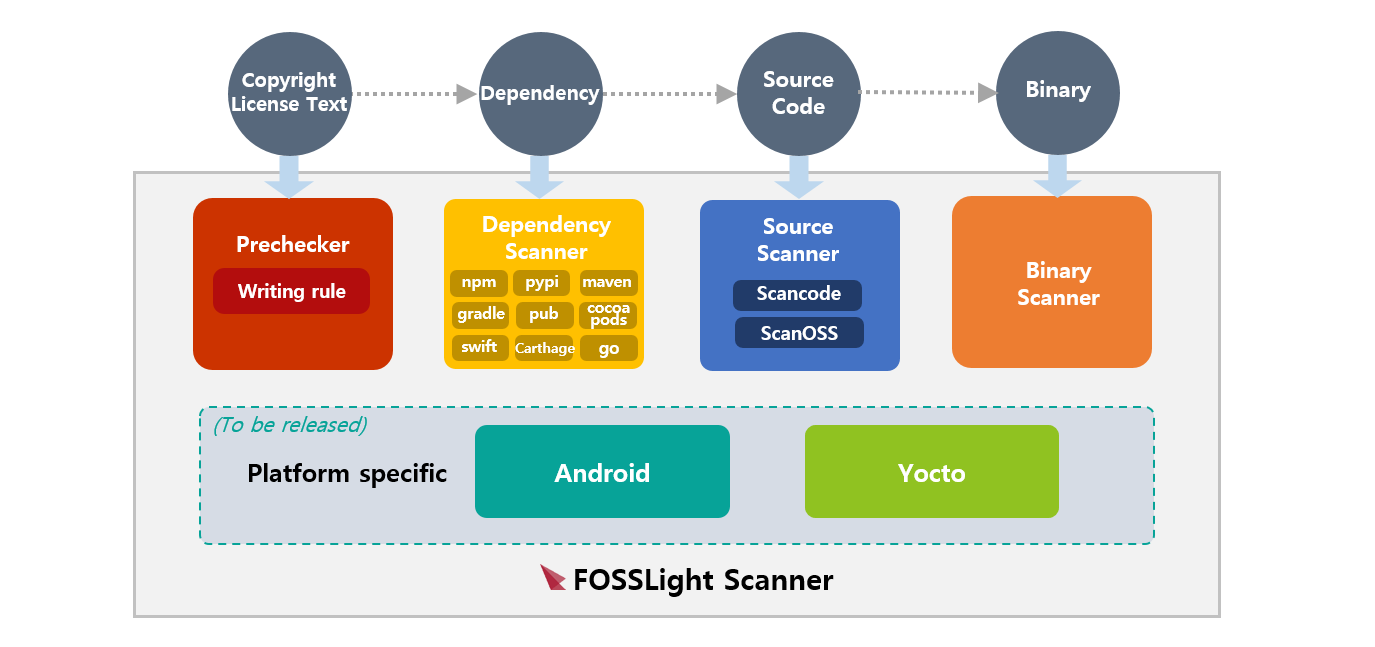

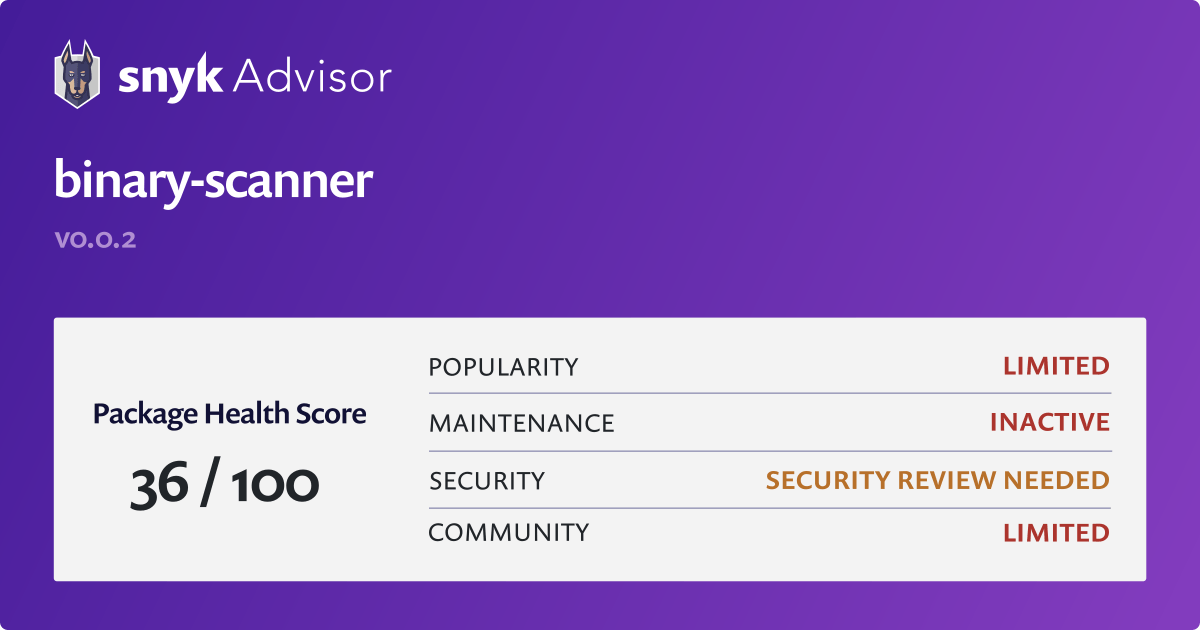



-1.jpg?width=577&name=Appknox%20Infographic-%20Binary%20Code%20Analysis%20vs%20Source%20Code%20Analysis%20(Medium)-1.jpg)