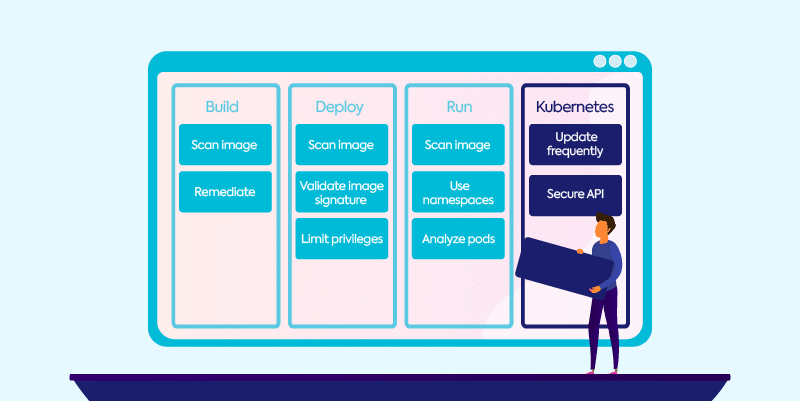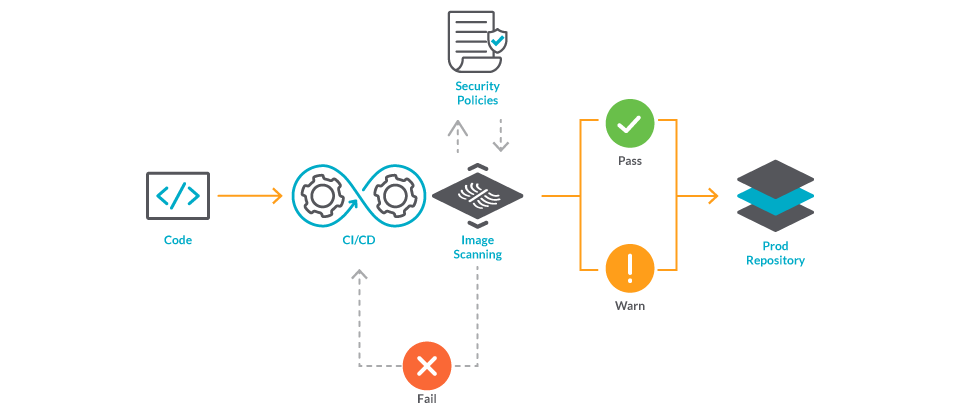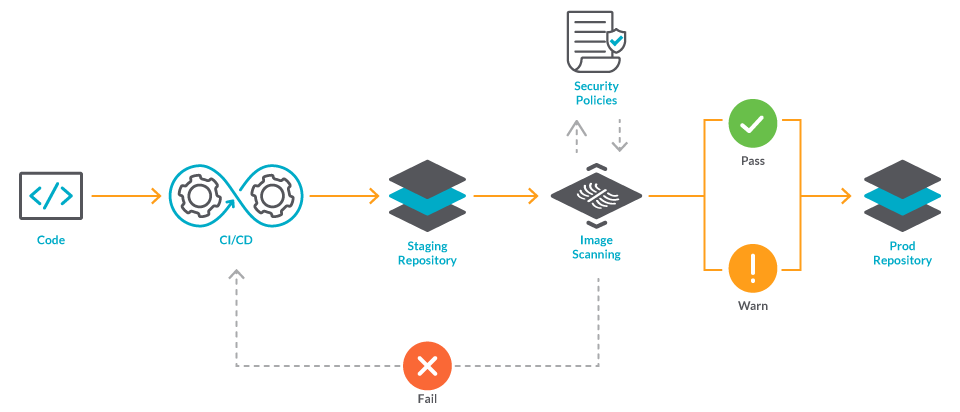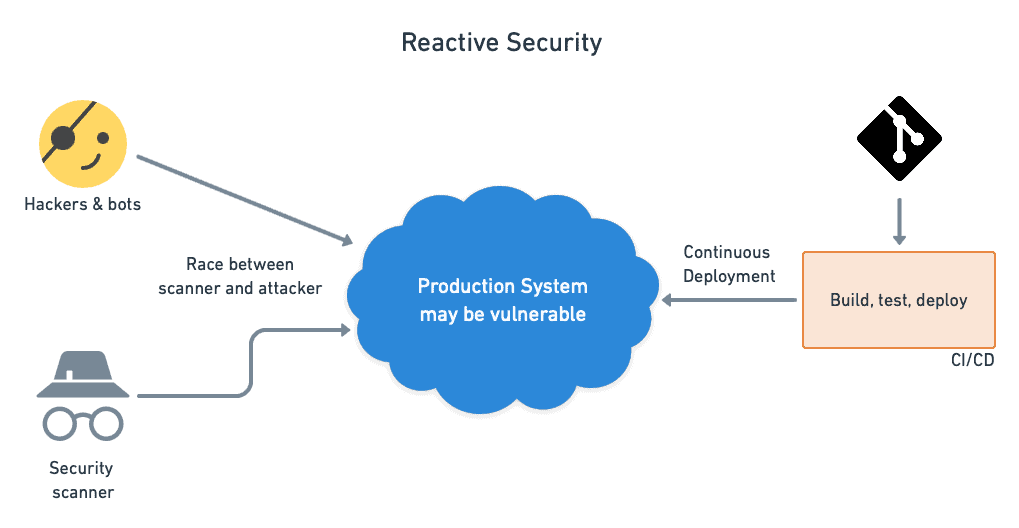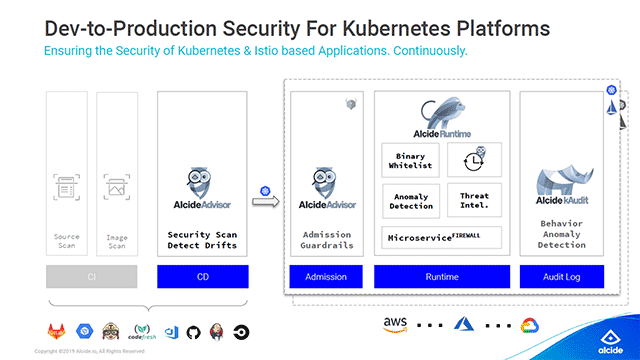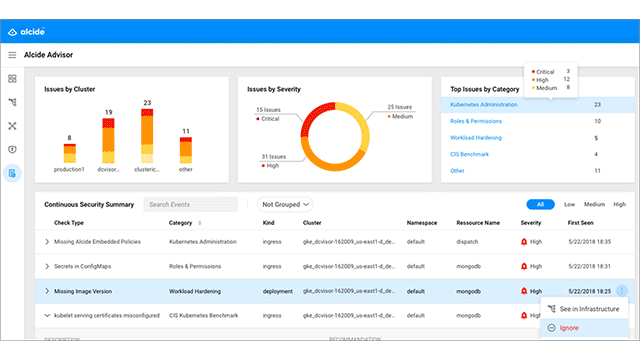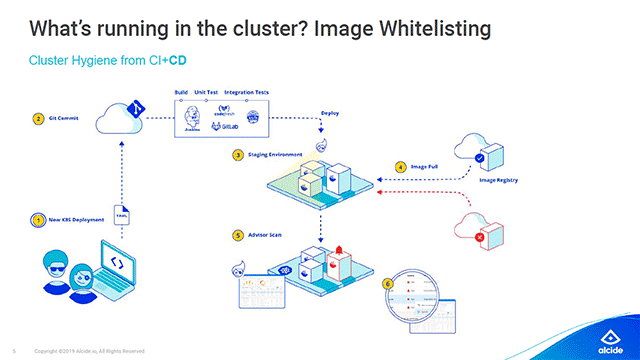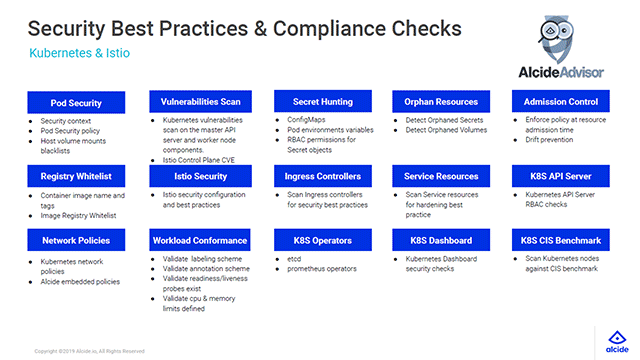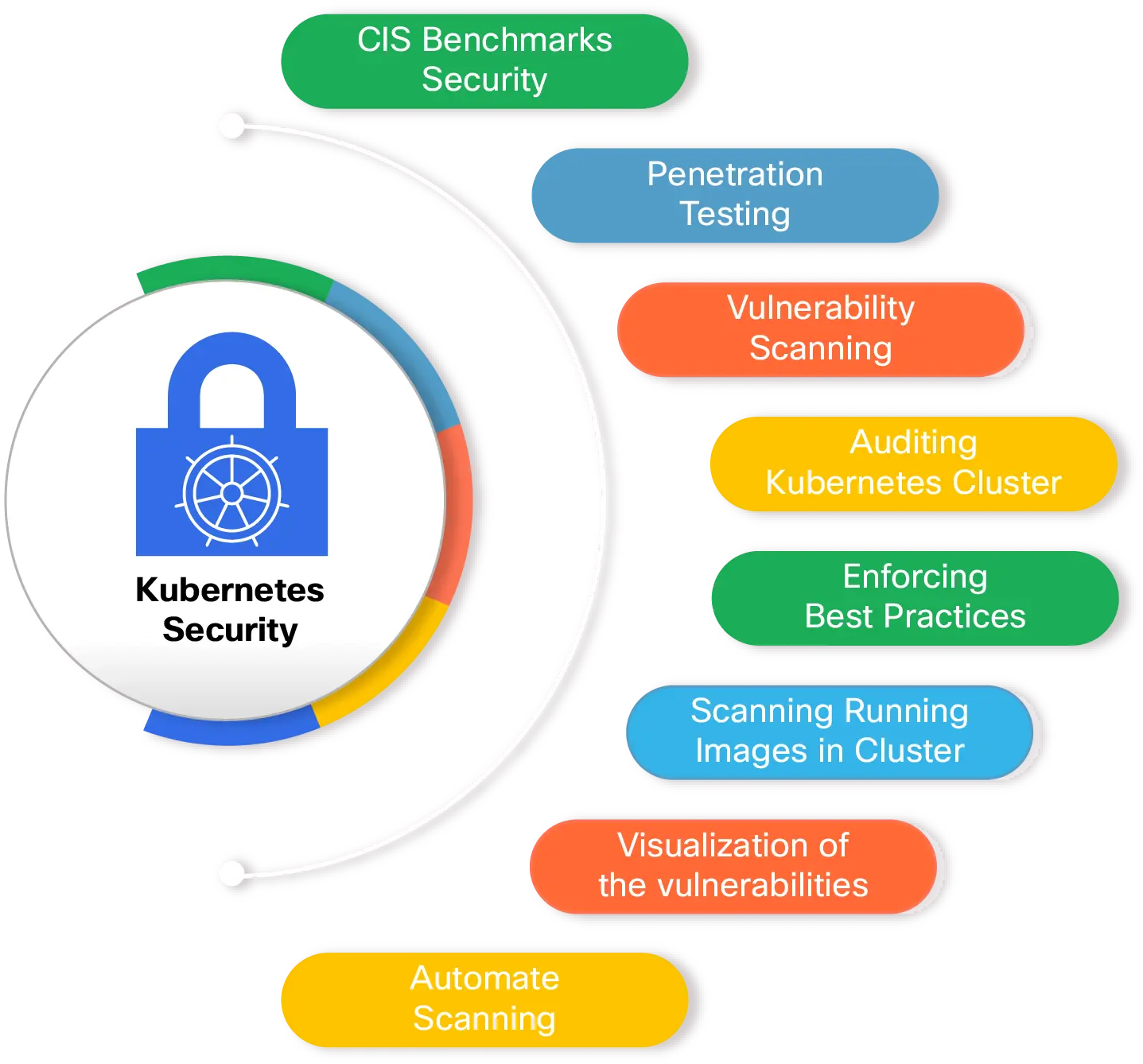
Cisco Panoptica Kubernetes Security for Cloud-Native Applications - Panoptica Kubernetes Security-Panoptica
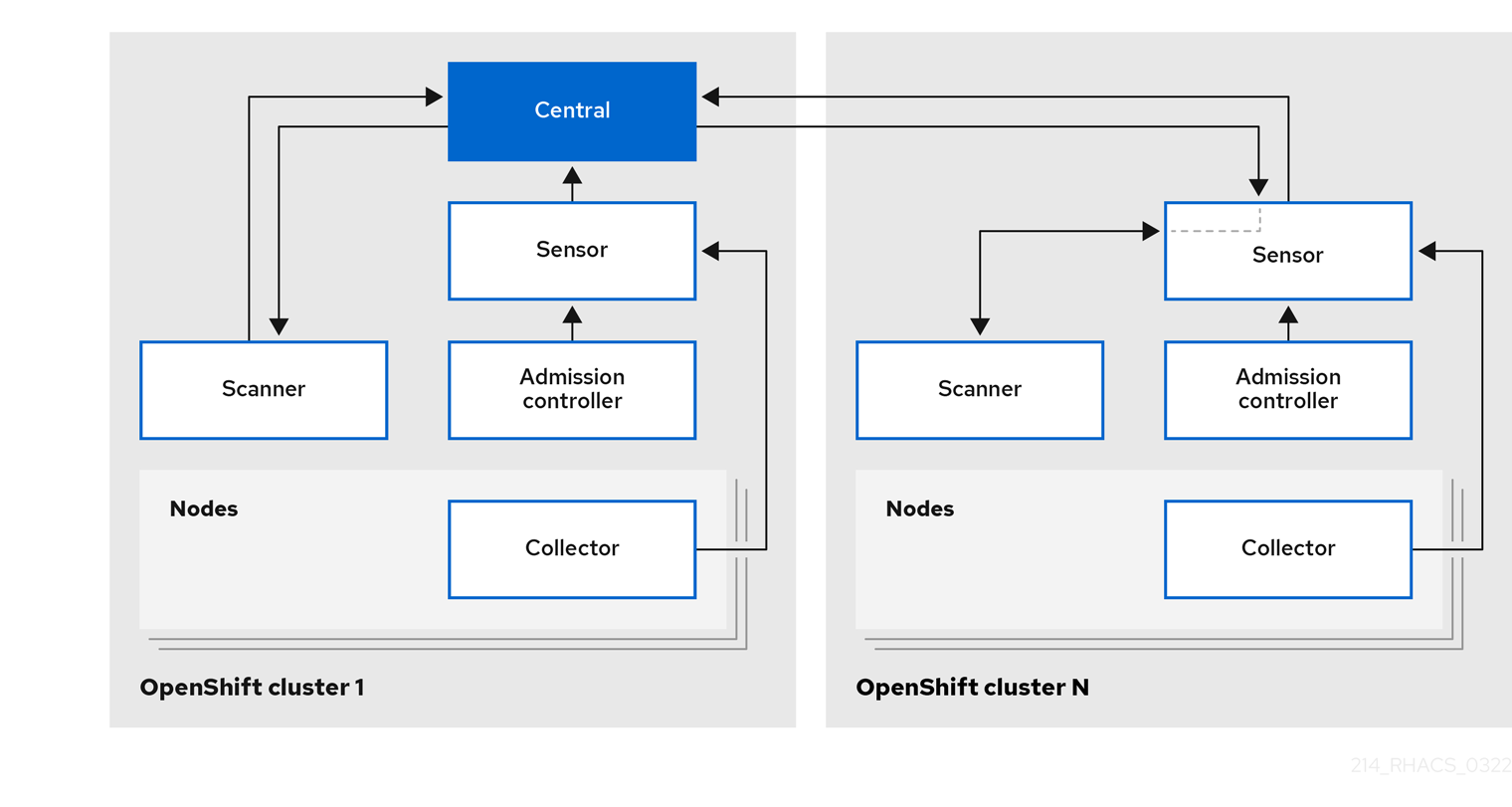
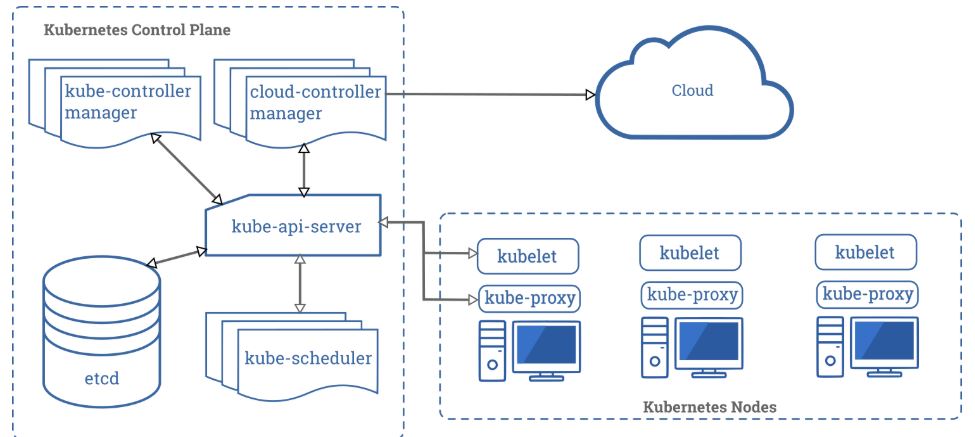
Chapter 1. Red Hat Advanced Cluster Security for Kubernetes architecture Red Hat Advanced Cluster Security for Kubernetes 3.70 | Red Hat Customer Portal
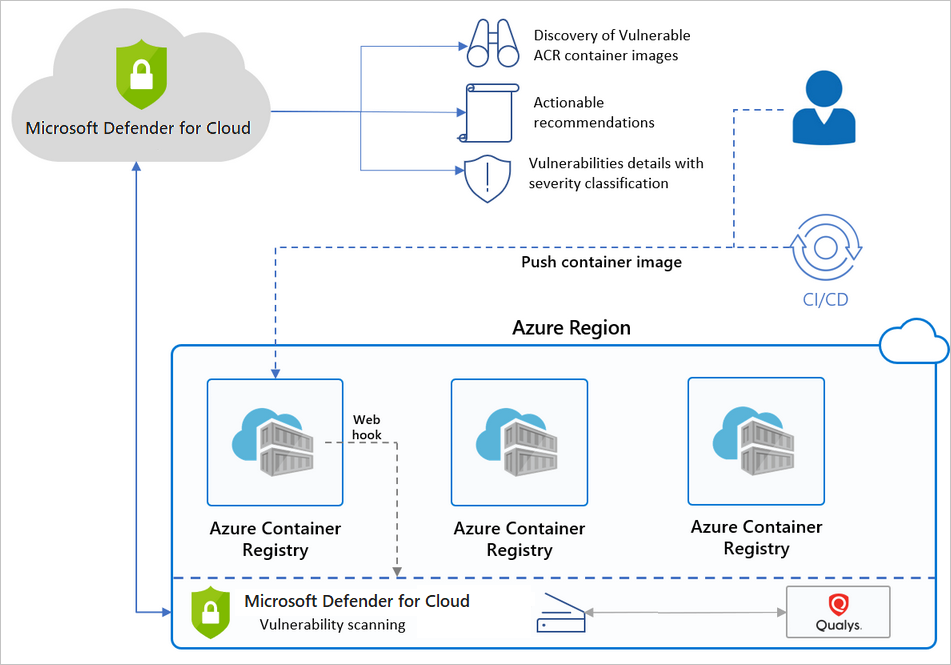
Microsoft Defender for container registries - the benefits and features - Microsoft Defender for Cloud | Microsoft Learn



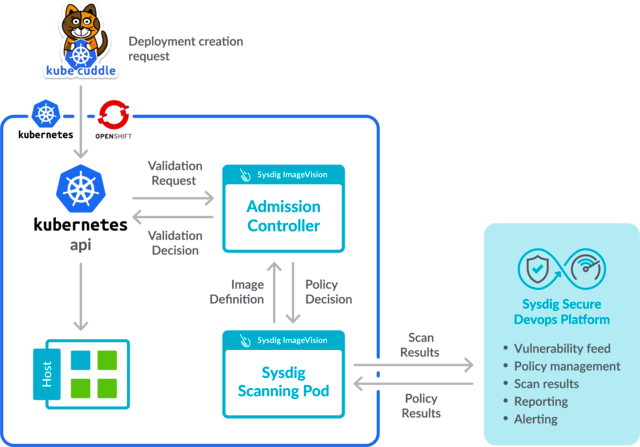
/filters:no_upscale()/news/2021/09/kubernetes-hardening-guidance/en/resources/1k8s-image-scanning-admission-controller-1631713081121.png)