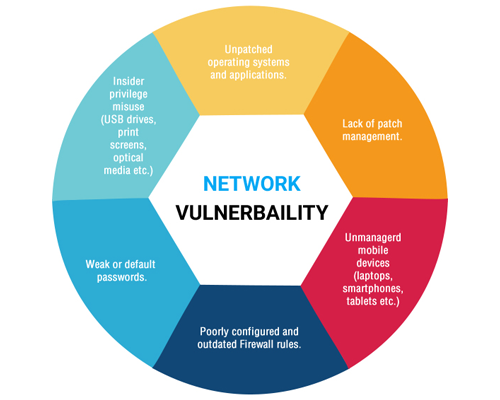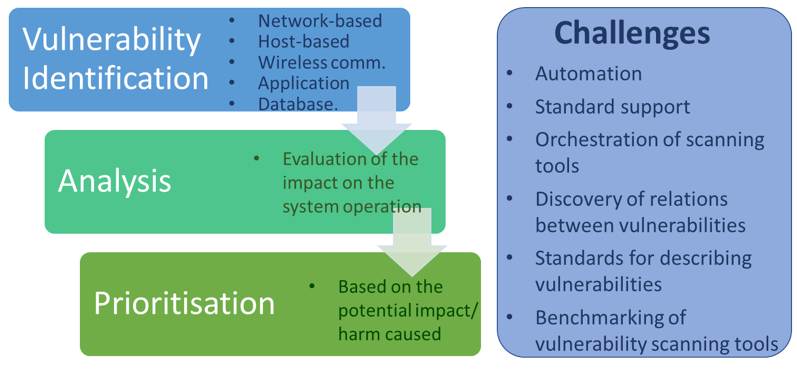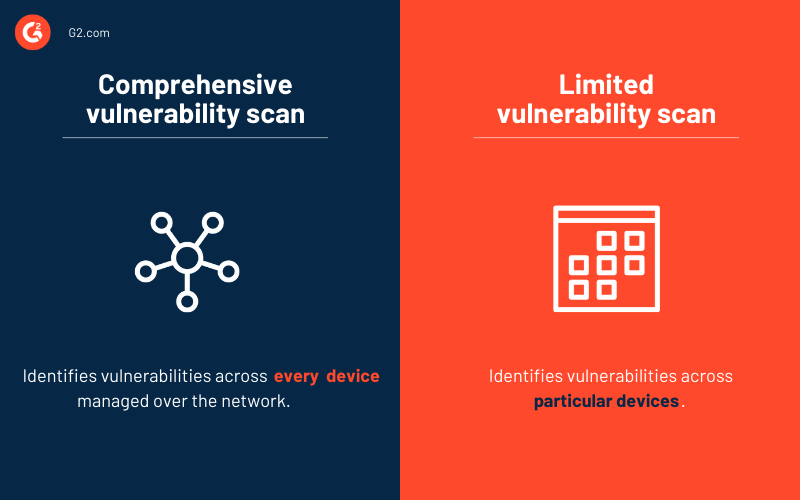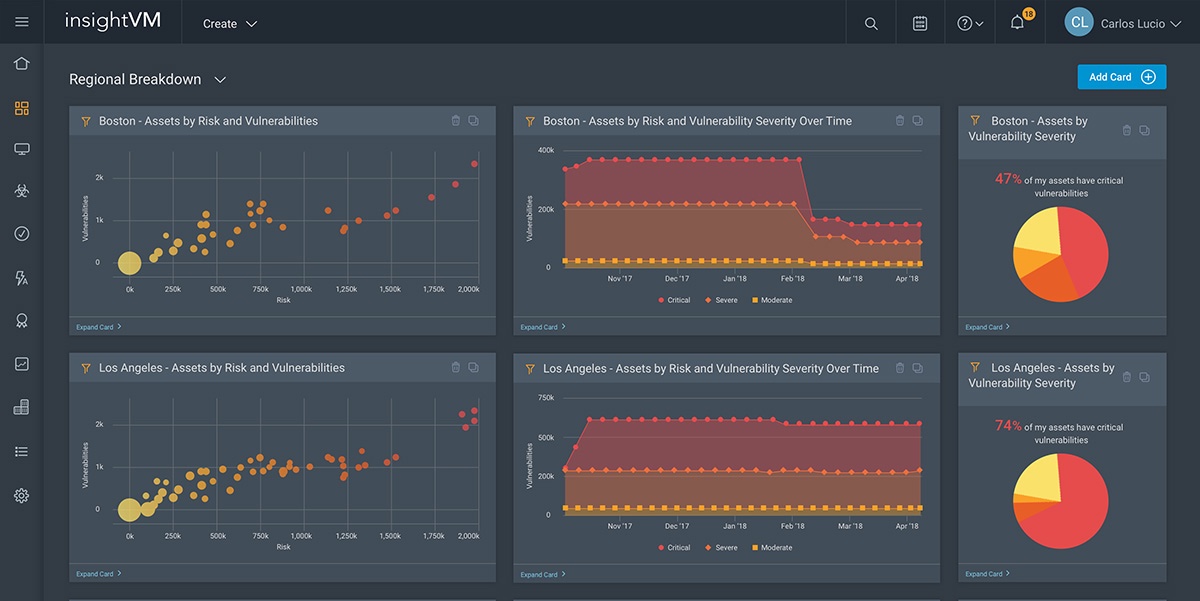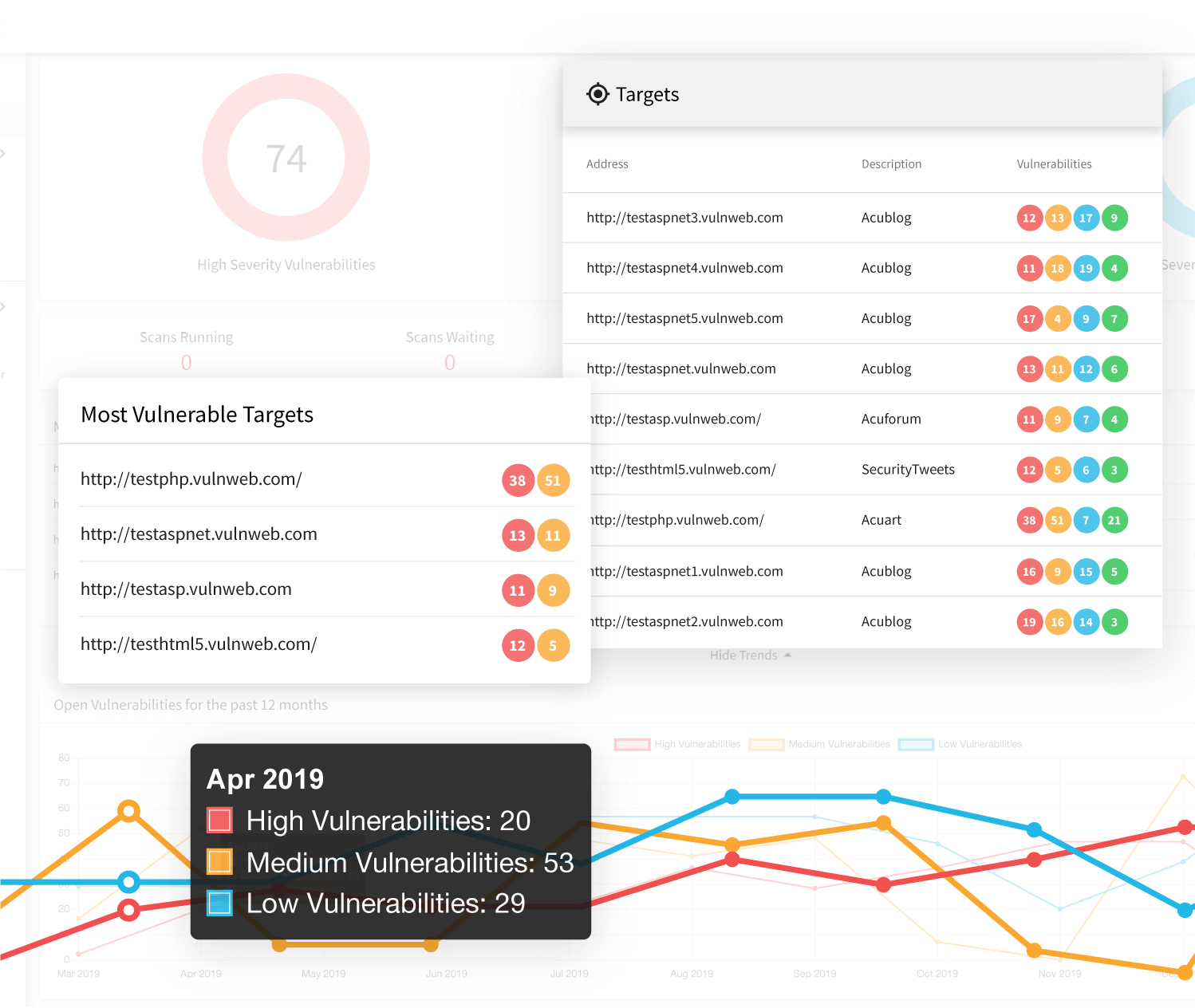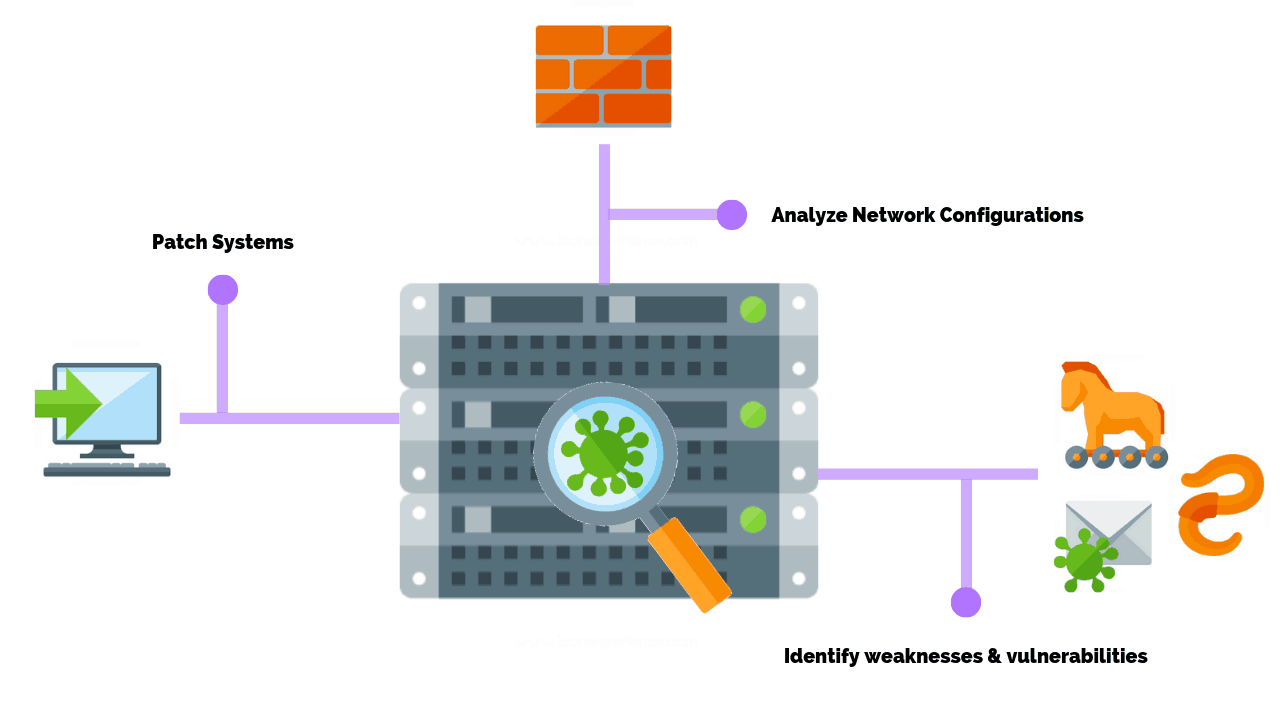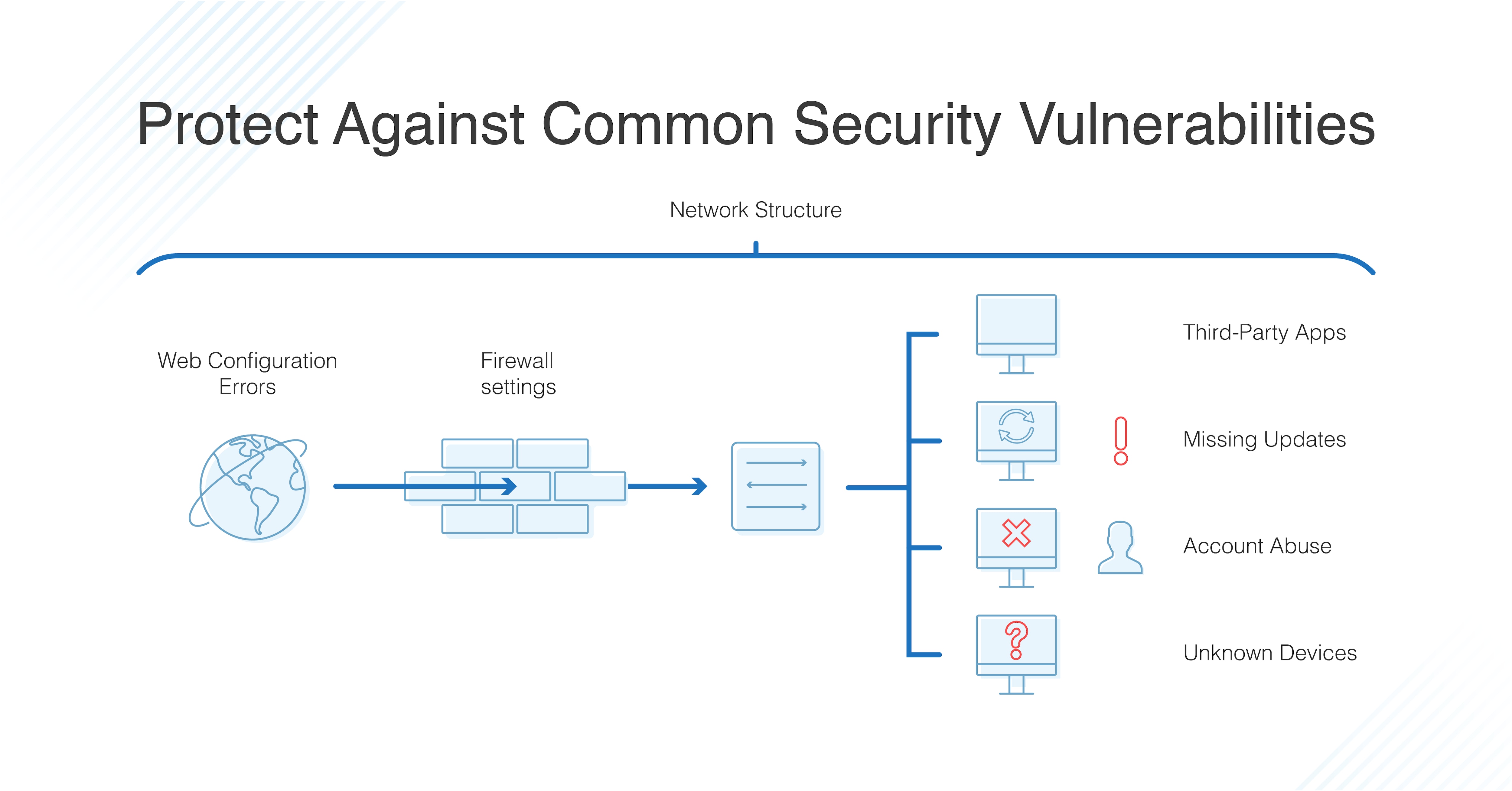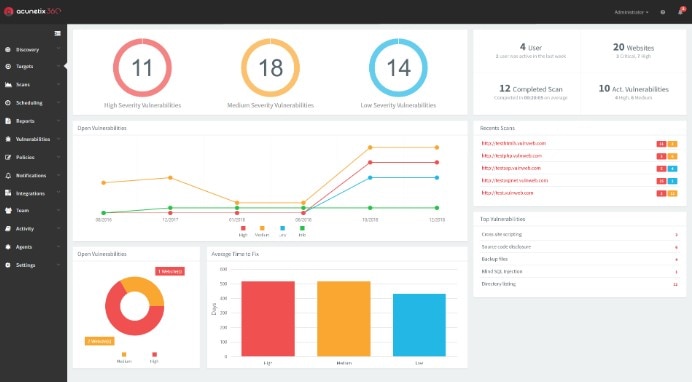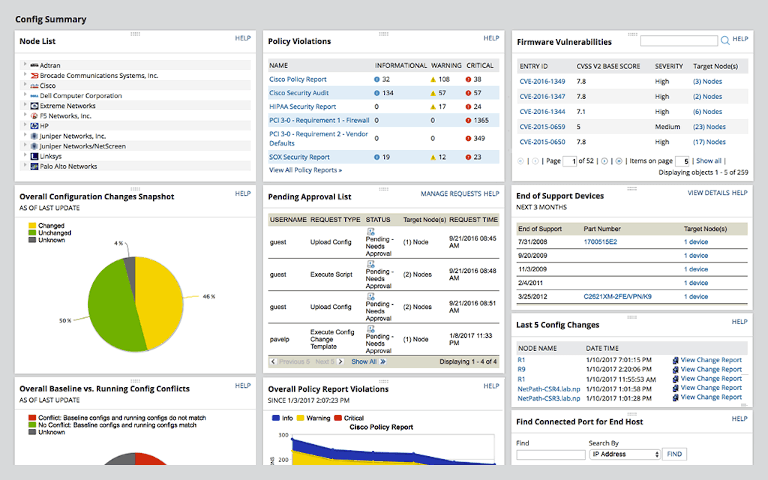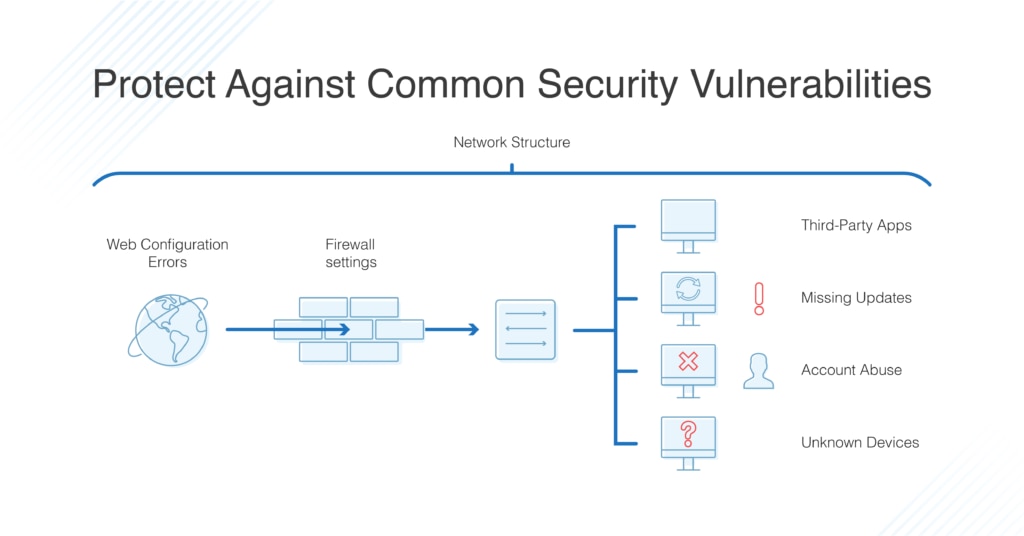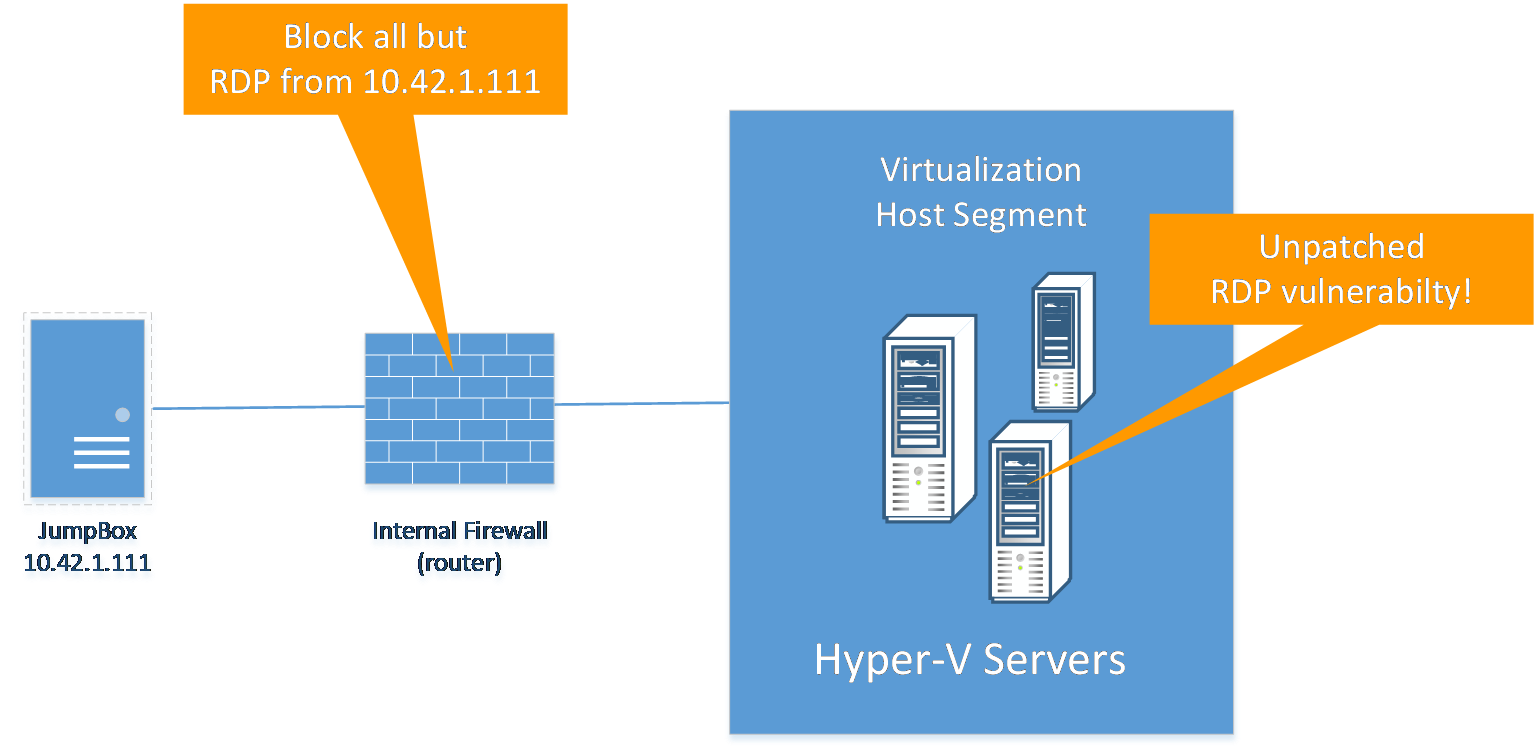
Correlating Vulnerability Scans with Network Path Analysis to Find and Remediate the Biggest Risks to Your Network and Avoid Wasting Time on the Little Ones
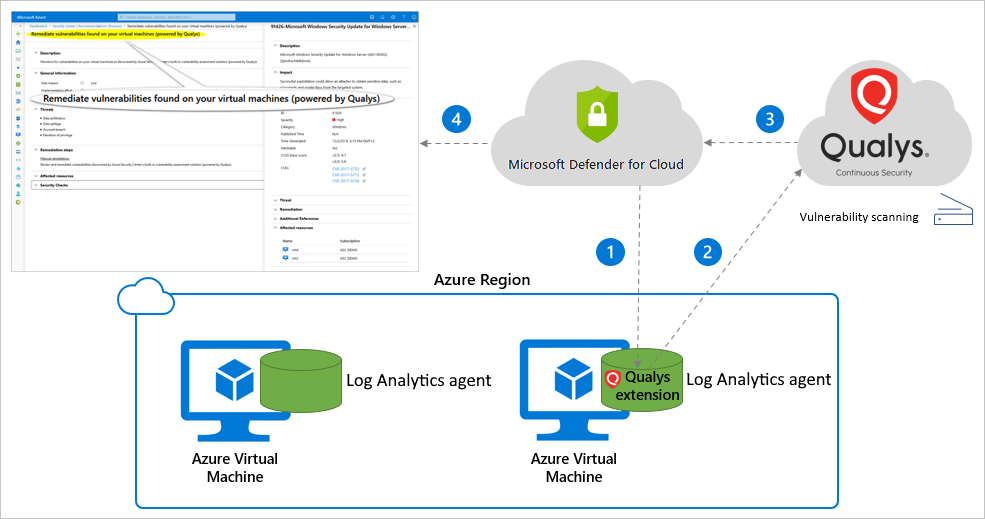
Enable vulnerability scanning with the integrated Qualys scanner - Microsoft Defender for Cloud | Microsoft Learn
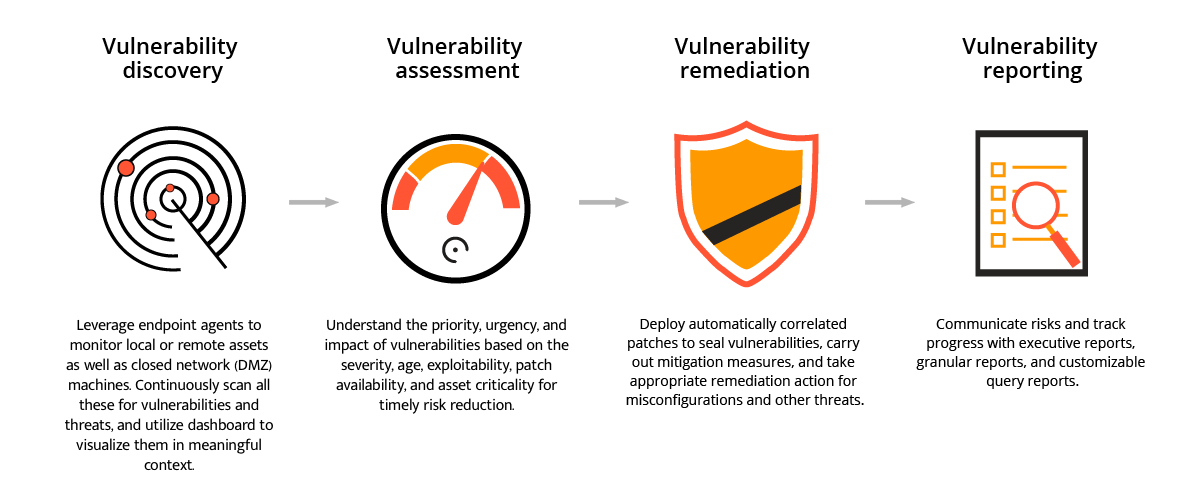
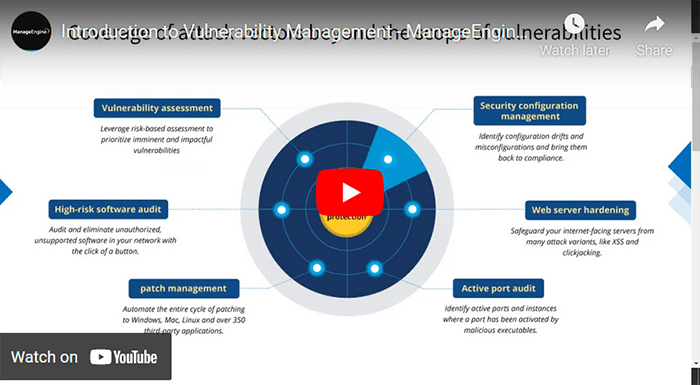
Vulnerability Scanner | Powerful Vulnerability Scanning Tools - ManageEngine Vulnerability Manager Plus